Honeypot: less noise, more certainty
Trapster deploys honeypots on your network to detect lateral movements, malicious scans and insider threats. Few false positives, instant alerts, and reduction of your detection time.
Designed by offensive security experts
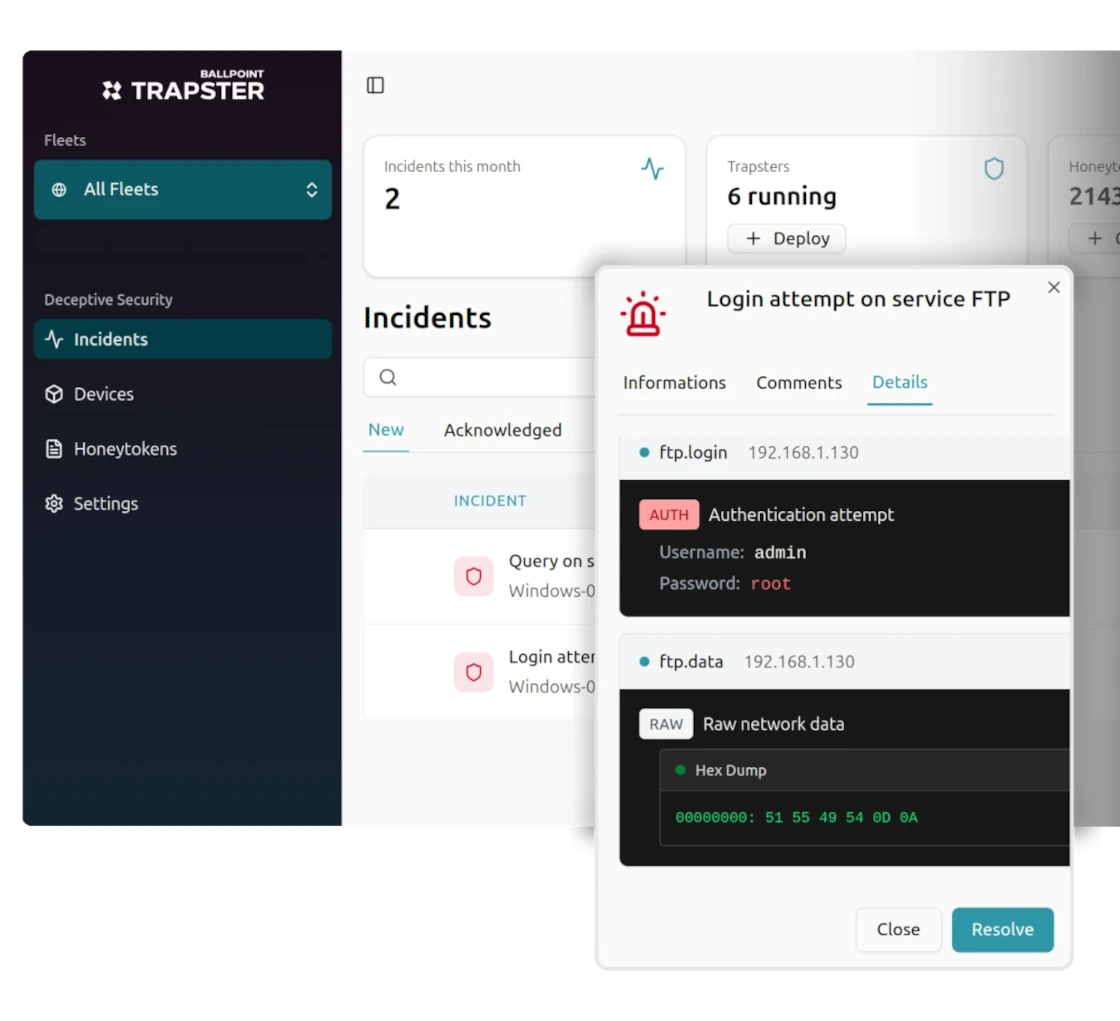
What is Deceptive Security?
A proactive cybersecurity approach based on deception
Deceptive Security (or deception technology) involves placing digital decoys in your infrastructure to detect attackers. These decoys have no legitimate purpose: any interaction with them is suspicious by definition.
Unlike traditional solutions (EDR, firewall, antivirus) that try to block known threats, Deceptive Security detects malicious behavior by luring attackers to fake systems.
It's a complementary detection layer that excels at identifying lateral movements, insider threats, and attacks that fly under the radar of traditional tools.
Honeypot
A complete system that simulates a real server or service (SSH, RDP, SMB, databases...). It attracts attackers and records their actions.
Honeytoken
Trapped data (fake credentials, decoy files, fake API keys). If someone uses them, an alert is triggered immediately.
Breadcrumb
Fake clues placed on your real systems to guide attackers toward honeypots (shortcuts, DNS entries, config files).
Why Trapster?
EDR/XDR are not enough
They detect known threats, but sophisticated attackers know how to bypass them. Lateral movements often go unnoticed.
Too many false positives
Traditional tools generate thousands of alerts, drowning real threats in noise. SOC teams are overwhelmed.
Detection too late
On average, an intrusion is detected after 200+ days. That's far too late to prevent major damage.
Trapster alerts you within the first minutes of an intrusion
High-fidelity alerts
Any interaction with a honeypot is suspicious by definition
Early detection
Detect scans and lateral movements immediately
Insider threats
Detect malicious or compromised employees
EDR complement
Adds a detection layer that EDRs don't cover
How does this work?
Download
pre-configured VMs and adapted to each enterprise
Fast installation
on the network (VMWare, Hyper-V or Proxmox)
Configuration
with a pre-configured template or a wide selection of services (HTTP, FTP, SSH, SMB, DNS, LDAP, etc.)
monitoring
Your trapsters monitor your network while you work
Reception
of an alert by email and notification on the dashboard
Analysis
of the alert
Login
with your other security tools to eliminate the threat
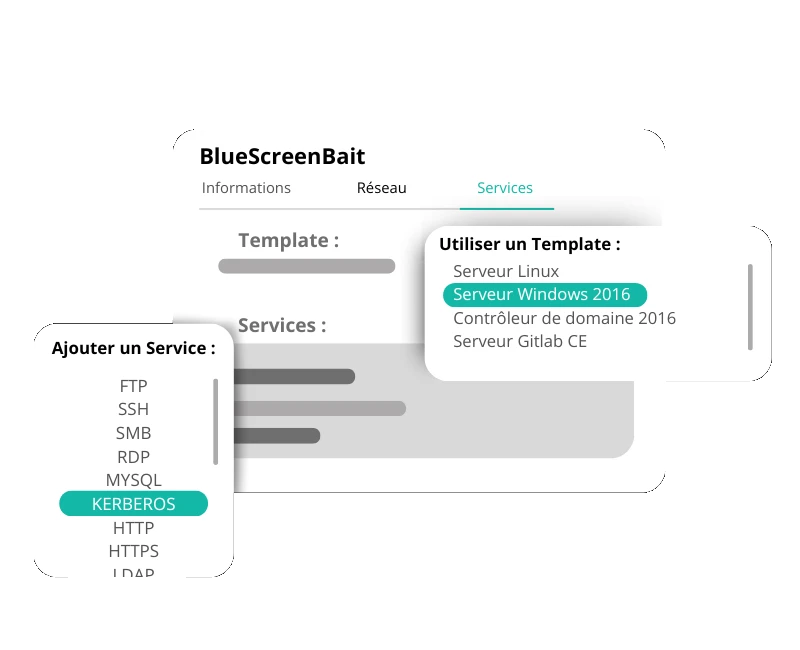
Adapts perfectly to your network
Trapster blends into your existing infrastructure. Customize every aspect so that honeypots look like your real systems.
- Services and ports are entirely personnalisables
- Ready-to-use templates for fast deployment
- Customizable banners and responses
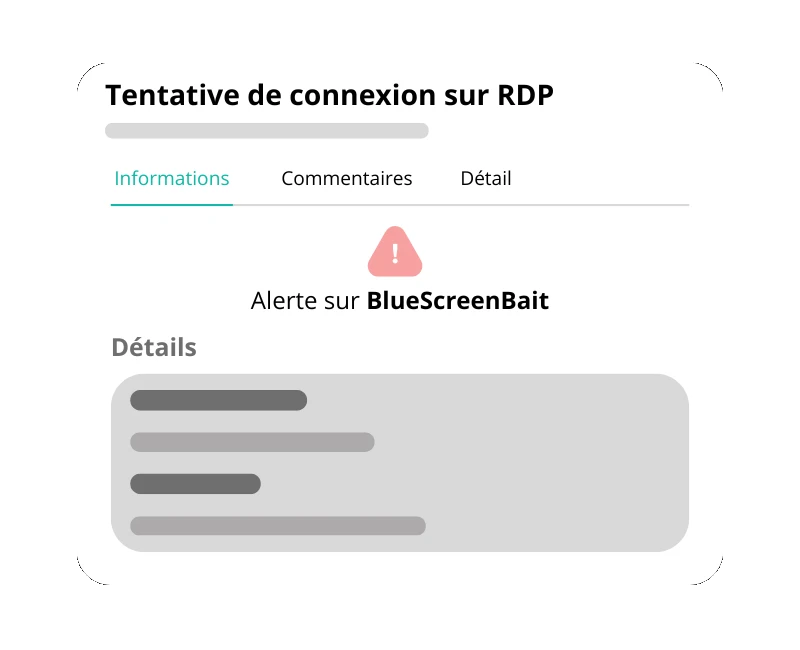
Get alerted instantly
As soon as a suspicious interaction is detected, receive a notification on your preferred channel with all the necessary context.
- Real-time dashboard with full context
- Email, Slack, Teams, Discord notifications
- SIEM integration via Syslog and REST API
Trapster watches over your network
So you can focus on your priorities
Fast installation
Deployment in minutes, automatic configuration
Easy to use
No advanced technical skills required
Few false positives
High-fidelity alerts, targeted investigation
French Cloud
Hosted on OVHCloud, developed in France


Member of Platform58
La Banque Postale's incubator supporting innovative startups in cybersecurity, Fintech and Regtech.

ISO 27001 Certified
Certified by BSI Group, ensuring the confidentiality, integrity and availability of your data.
A product of Ballpoint
Designed by offensive security experts
Our finding after hundreds of penetration tests: too few companies detect attacks in time. EDR/XDR solutions are often bypassed by experienced attackers.
Trapster was born from this field reality. As pentesters, we know that a well-placed honeypot is one of the most effective tools for detecting an intrusion.
Ready to secure your network?
Try Trapster free for 14 days. Deployment in 5 minutes, no credit card required.







