Principle of Trapster
Problem
Here’s the situation. Conventional security products?
Of course, they can be robust. But there’s a catch:
The noise.
For most businesses, the volume of security alerts is overwhelming, causing time and money to be wasted on endless sorting and verification.
It's exhausting and not always effective.
Solution
What if your security system could outsmart attackers without worsening your alert fatigue?
Here is the honeypot.
This is not just an additional tool in the arsenal: it is the most intelligent way to improve security.
By placing what seems to be valuable targets, we don't chase attackers; we make them come to us.
This means we only alert you when a real threat is detected, significantly reducing the noise. Our honeypots are meticulously designed to catch even the craftiest new attackers, without having to identify every new attack method available.
Instead of searching for threats, you attract them into a trap.
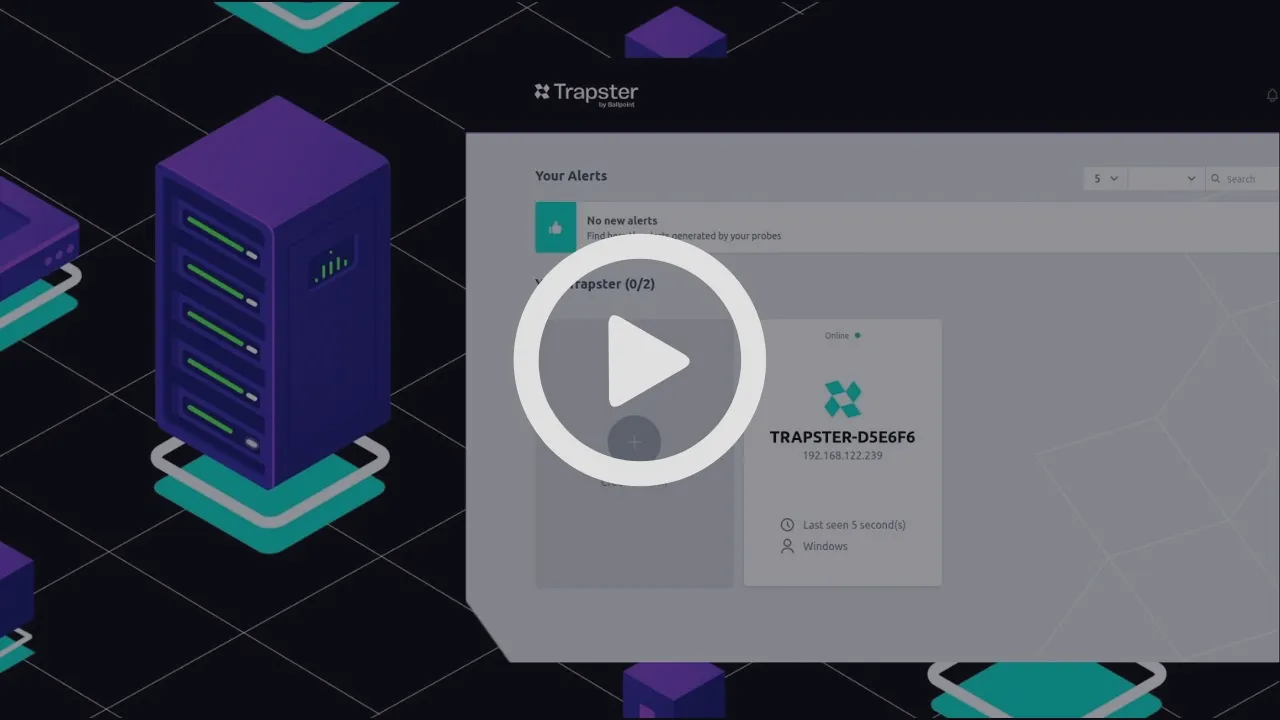
Deployment
The deployment of Trapster is transparent and does not overload your existing security team.
These decoys easily integrate into your network, mimicking valuable assets without requiring constant monitoring or generating false alerts.
They operate silently in the background until an attacker is revealed, giving you high-quality alerts that truly count.
This setup not only saves time and resources but also shifts the balance of power, allowing you to observe, learn, and therefore have several steps ahead of the cybercriminals.
Capture criminals, not just noise.