Integrate Trapster on ELK
test

What is the CEF format ?
The CEF (Common Event Format) is a standardized way to record and receive security logs (syslog). Because CEF is standardized, you can use it to collect and process data from many different sources.
Trapster uses the CEF format to transmit events via SYSLOG. It is also possible to process events from your dashboard via webhooks, which can integrate into existing systems.
CEF allows you to analyze the origin of attacks or the target systems of attackers, as well as correlate events between machines to better understand how an attack has spread.
This article explains how to integrate Trapster with ELK using SYSLOG and the CEF format.
Typical CEF logs use the following format:
CEF:Version | Device Vendor | Device Product | Device Version | deviceEventClassId |Name | Severity | Extension
CEF:
- Version: CEF version can be 0 or 1
- Device Vendor (here Ballpoint)
- Device Product: sold product - here it is Trapster
- Device Version: Product's current version
- DeviceEventClassId: A unique login for each type of event: This field should include the protocol with which the attacker interacted, such as VNC or FTP.
- Name: A human-readable sentence to describe the event: Here, you can see the type of attack, such as 'login'.
- Severity: The severity is always a number between 0 and 10 or a word like low, medium, high, or very-high.
- Extention: Here, we can include any other relevant information such as the source IP, a clearer message to describe the event, or the OS pattern you have chosen for your Trapster.
To better understand, here is an example of what you might see from Trapster, including where the attack is coming from, the protocol used, and the type of attack. You will see the same information as on your dashboard:
<128> CEF:1|Ballpoint|Trapster|v1.0|VNC|login|10|src=157.171.84.63 dst=122.251.101.180 msg=Login attempt on VNC
Integration with ELK (Elasticsearch, Logstash, Kibana)
ELK integrates the components Elasticsearch, Kibana, Beats, and Logstash to process your CEF syslog logs. It is widely used because it allows easy collection and visualization of data. The Trapster dashboard can send logs via Syslog using UDP or TCP. Simply provide us with the IP address and port of your ELK installation.
CEF Format
You need to add the CEF plugin to process the logs in ELK. You can find the open-source plugin here: https://github.com/logstash-plugins/logstash-codec-cef
If your Logstash is running in a Docker container, you can install this plugin via the Dockerfile. Add the line "RUN logstash-plugin install logstash-codec-cef" to your file in docker-elk > logstash > Dockerfile to install it, then restart your Docker.
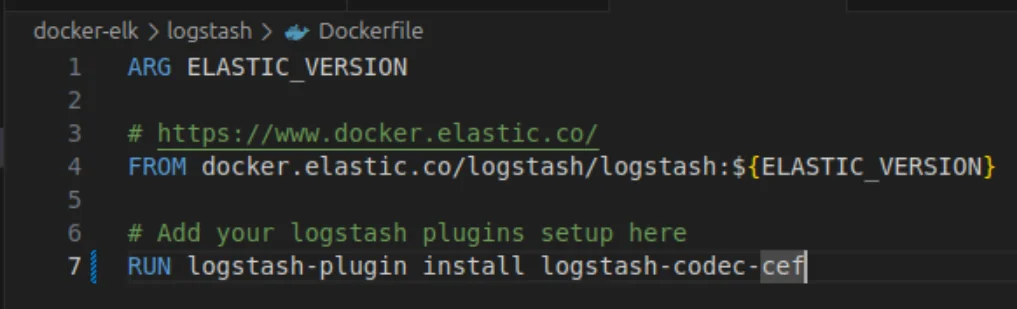
Now that you have the plugin you can specify the formatting of logstash. Go to Docker-Elk> Logstash> pipeline> Logstash.conf and add the following configuration:
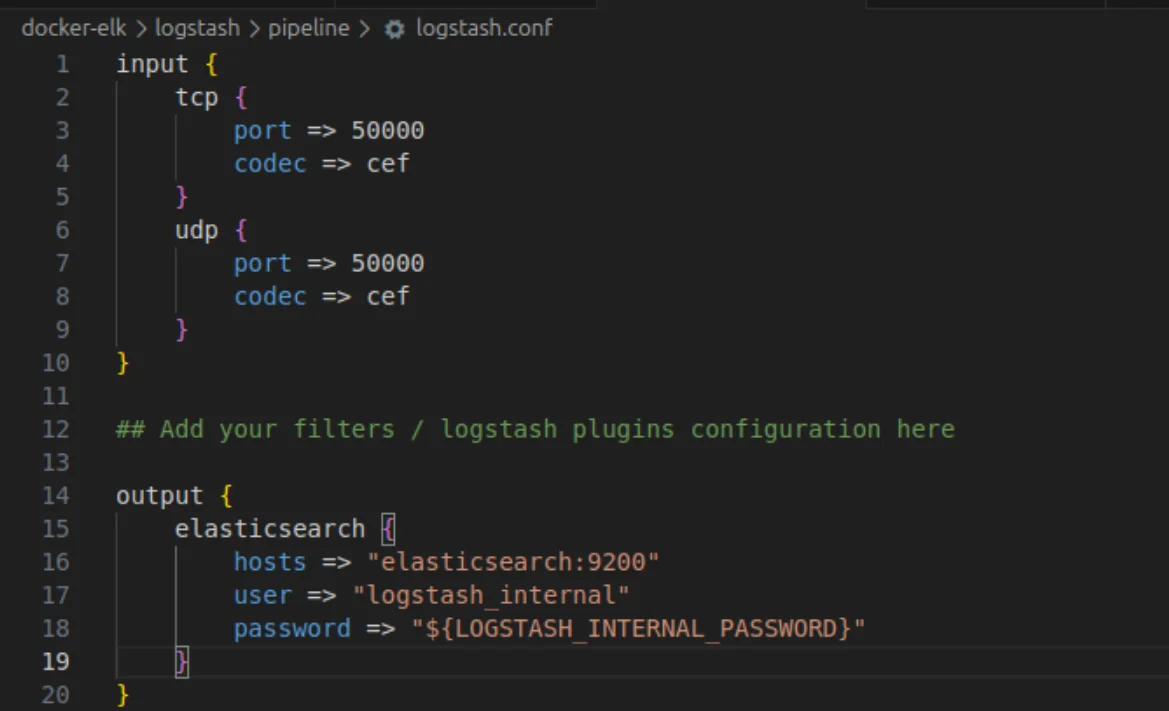
- Codec: To properly filter the CEF logs.
- Port: To specify the open port. Here, you should enter the port you decided on earlier, but you can use the same port for both UDP and TCP.
Kibana's configuration
On your Kibana page, you should now see the captured logs. On your Trapster settings page, you can send a test message to ensure everything is working. If not, make sure your network is correctly configured so that Logstash can receive events.
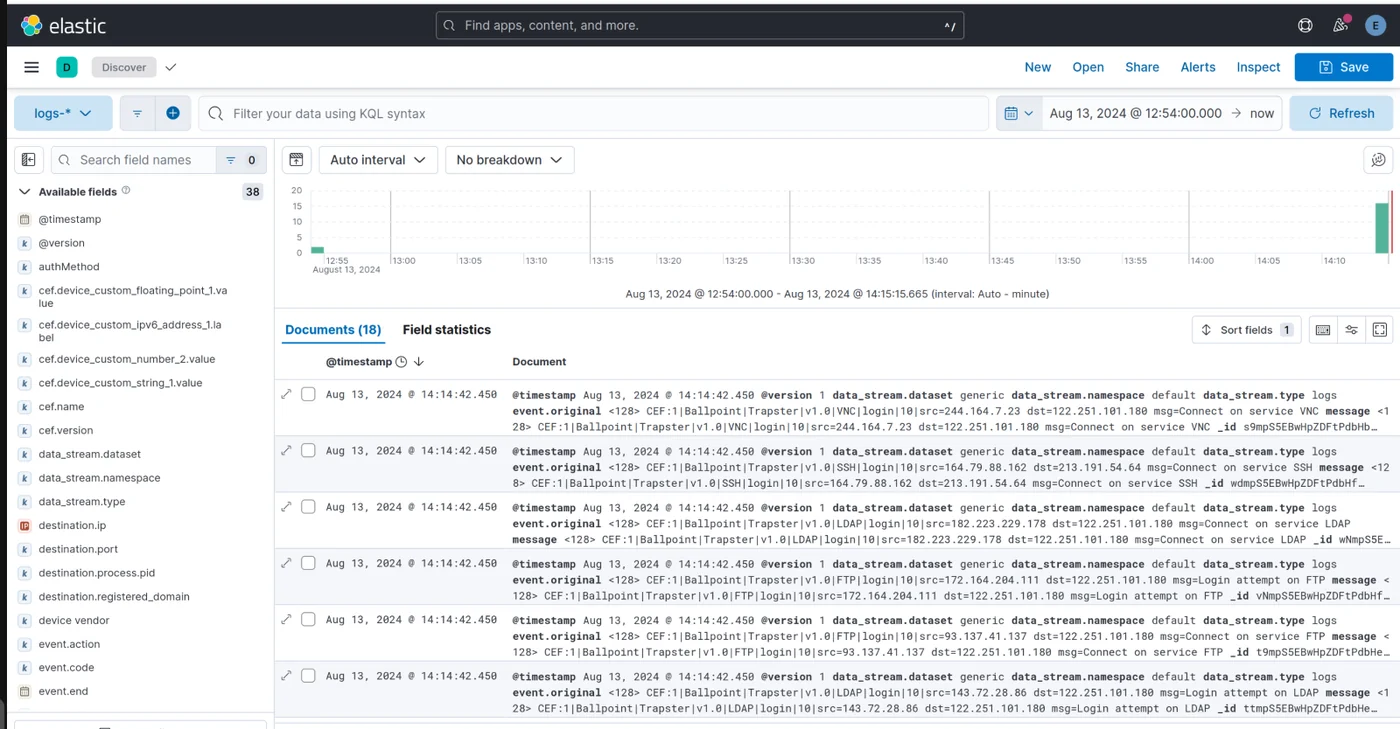
However, you may notice that the data is not being correctly processed in CEF format in Kibana because Kibana doesn't know it's in CEF format.
To tell Kibana how to analyze the data, you need to create a data view. Online, you may see many references to "index patterns," which is the old name for "data views."
In "Management > Kibana > Data Views," you can create a data view with the name you prefer.
Select the index pattern, such as cef-logs-*, corresponding to the format you provided earlier in logstash.conf to index your data.
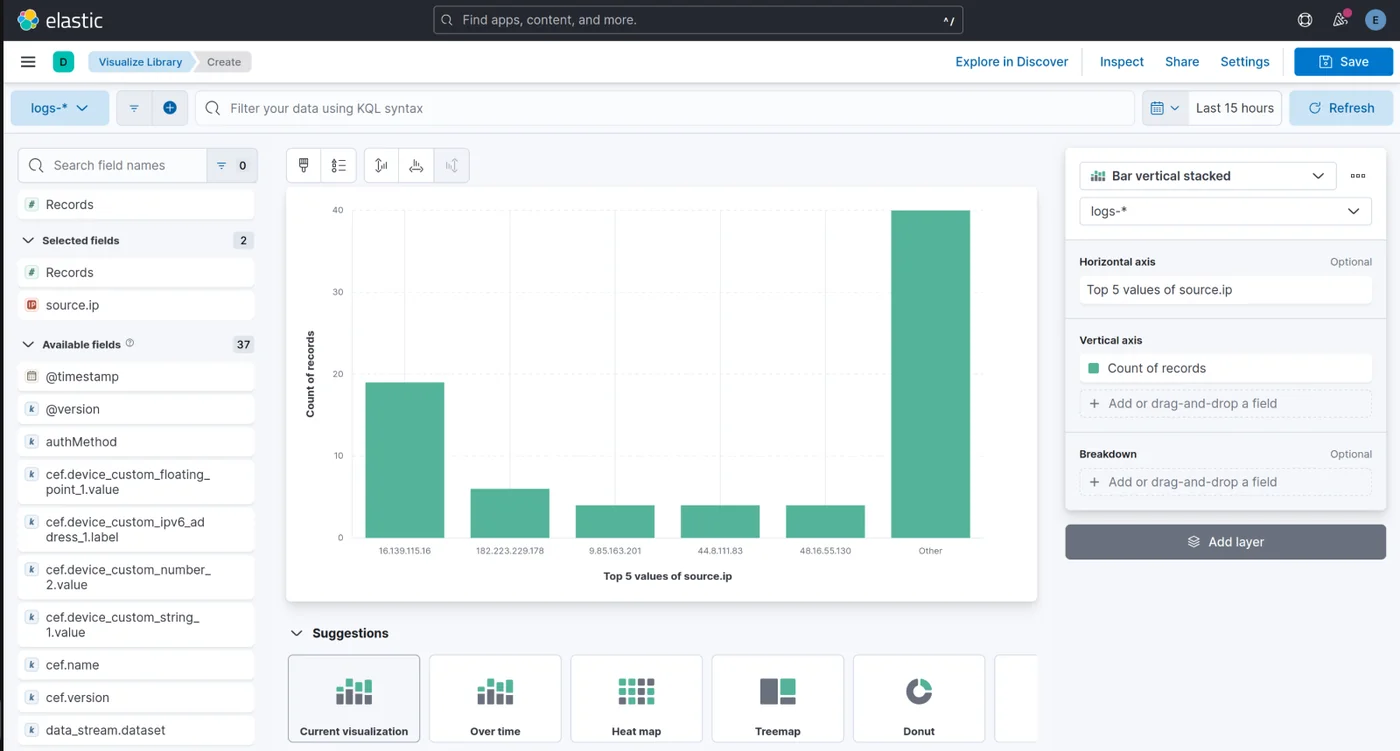
Afterward, in "Analytics > Discover," you can now select your "data view." With Kibana, you can easily visualize the data and create charts to see which of your Trapsters is receiving the most traffic.
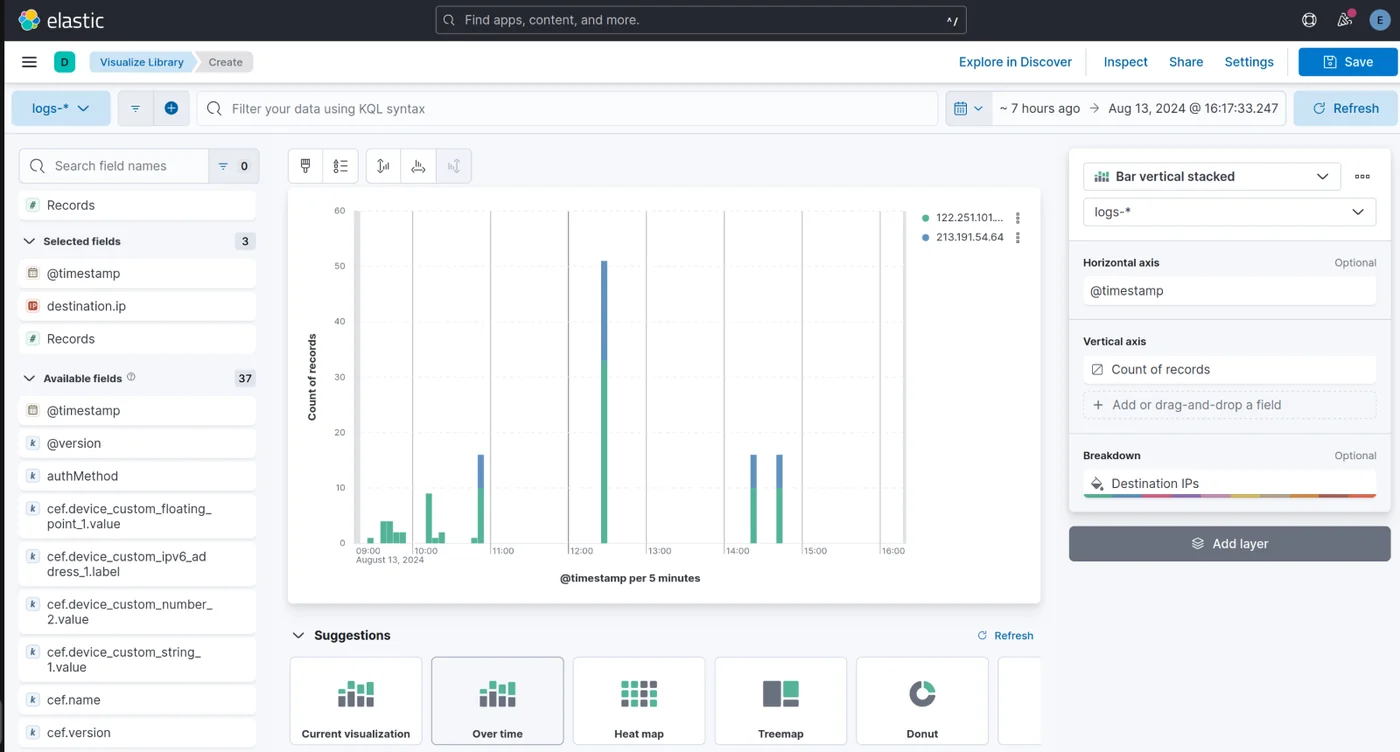
Or even, where the attacks are coming from: You can also create alerts for specific events in "Security > Alerts".
Here, you can choose to receive alerts if there is an event with a certain IP or a severity level above a specified threshold.